
Spring Semester, 2005
Some Parsing & Security
© 2005, All Rights Reserved, SDSU & Roger Whitney
San Diego State University -- This page last updated 03-Feb-05

|
Client-Server Programming
Spring Semester, 2005 Some Parsing & Security |
|
|---|---|---|
|
© 2005, All Rights Reserved, SDSU & Roger Whitney San Diego State University -- This page last updated 03-Feb-05 |
Copyright ©, All rights reserved. 2005 SDSU & Roger Whitney, 5500 Campanile Drive, San Diego, CA 92182-7700 USA. OpenContent ( http://www.opencontent.org/opl.shtml) license defines the copyright on this document.
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 2 |
Java Network Programming, Harold, O’Reilly, pp 67-104
Applied Cryptography Second Edition, Bruce Schneier, John Wiley & Sons, 1996
VisualWorks Security Guide, pp 17-23
BitTorrent Specification http://wiki.theory.org/BitTorrentSpecification
Java Network Programming, Harold, O’Reilly, pp 67-104
BitTorrent Specification http://wiki.theory.org/BitTorrentSpecification
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 3 |
'li2e3:cate'
How to parse the above bencoded string?
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 4 |
Example: Gnutella Message Header
|
|
Desciptor ID |
Payload Descriptor |
TTL |
Hops |
Payload Length |
||
|
Byte offset |
0 |
15 |
16 |
17 |
18 |
19 |
22 |
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 5 |
li2ei345ee <h1>A Header</h2> java=properties file=example HTTP/1.1 200 OK Date: Tue, 05 Sep 2000 19:31:14 GMT Server: Apache/1.3.9 (Unix) PHP/3.0.12 Last-Modified: Mon, 04 Sep 2000 21:03:56 GMT
Special characters indicate start and/or end of a token
In Bencoding lists, integers & dictionaries use this
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 6 |
What happens if the token contains the special character?
Example: C-based strings
“One line\nSecond Line\n”
\ indicates the next character is special
How to include the \ character in a string
“One line\\nStill one line”
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 7 |
3:cow4:spam
Note that in BEncoding the size is indicated using a special character
Why doesn’t BEncoding use special character to demark start & end of a string?
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 8 |
"cat;man;ran".split(";");
Returns an array of String [ “cat”, “man”, “ran”];
See http://java.sun.com/j2se/1.4.2/docs/api/java/util/regex/Pattern.html#sum
for valid arguments of split().
parts = new java.util.StringTokenizer("cat,man;ran;,fan", ",;");
while (parts.hasMoreElements())
{
System.out.println( parts.nextToken());
}
cat man ran fan
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 9 |
'cat;man;ran' tokensBasedOn: $;
OrderedCollection ('cat' 'man' 'ran')
'cat. man... ran.'
piecesCutWhere:
[:each :next | each = $. and: [next = Character space]]
do: [:each | Transcript show: each printString; cr]
'cat.' ' man...' ' ran.'
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 10 |
'cat\man\ran'
runsFailing: [:each | each = $\]
do: [:each | Transcript show: each; cr]
cat man ran
'cat\man\ran'
runsSatisfying: [:each | each ~= $\]
do: [:each | Transcript show: each; cr]
cat man ran
CS 580 Spring 05 Doc 4, Some Parsing & Security Slide # 11
Java Streams do not have many methods that aid in parsing
read()
Avoid PrintStream – println() is platform dependent
“PrintStream is evil and network programmers should avoid it like the plague”
Text claims that readLine() is buggy
Avoid using this method to read data from a socket
Are used for binary data
Don’t use unless protocol is binary
If protocol is binary these streams are only good between Java clients and servers
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 12 |
peek
Answer what would be returned with a self next, without changing position. If the receiver is at the end, answer nil.
peekFor: anObject
Answer false and do not move the position, if the next object is not anObject, or if the receiver is at the end. Answer true and increment the position if the next object is anObject.
skipToAll: aCollection
Skip forward to the next occurrence (if any) of aCollection. If found, leave the stream positioned before the occurrence, and answer the receiver; if not found, answer nil, and leave the stream positioned at the end.
throughAll: aCollection
Answer a subcollection from the current position through the occurrence (if any, inclusive) of aCollection, and leave the stream positioned after the occurrence. If no occurrence is found, answer the entire remaining stream contents, and leave the stream positioned at the end.
upTo: anObject
Answer a subcollection from position to the occurrence (if any, exclusive) of anObject. The stream is left positioned after anObject. If anObject is not found answer everything.
upToAll: aCollection
Answer a subcollection from the current position up to the occurrence (if any, not inclusive) of aCollection, and leave the stream positioned before the occurrence. If no occurrence is found, answer the entire remaining stream contents, and leave the stream positioned at the end.
skipUpTo: anObject
Skip forward to the occurrence (if any, not inclusive) of anObject. If not there, answer nil. Leaves positioned before anObject.
next: anInteger
Read the next anInteger elements
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 13 |
upToAll: is a useful method
http://www.eli.sdsu.edu/java-SDSU/docs/sdsu/io/ChunkReader.html
Reads up to a given string in a stream or string
read = new sdsu.io.ChunkReader("catEOMmatEOM", "EOM")
while (read.hasMoreElements() )
{
System.out.println( read.readChunk());
}
cat mat
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 14 |
(\+|-)?\d+(\.\d*)?((e|E)(\+|-)?\d+)?
Java & Smalltalk support Regular expressions
Sun Regular Expression Tutorial
http://java.sun.com/docs/books/tutorial/extra/regex/index.html
See
VisualWorks
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 15 |
<Term> := <Integer> | <List> | <Dictionary> | <String> <Integer> := i <digit>* e <List> := l <Term>* e <digit> := 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 <Dictionary> := d (<String><Term>)* e <String> := n:<character>n <character> := a | b | ...
Compiler Compilers
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 16 |
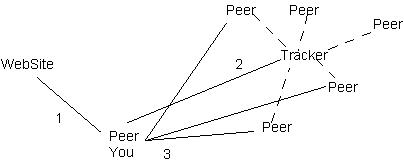
Step 1
You contact a BitTorrent web site You get information about a file
Step 2
You contact the BitTorrent Tracker for the file Tracker provides information about peers with parts of the file
Step 3
You contact peers for parts of the file
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 17 |
Some Possibilities
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 18 |
Two basic types of encryption:
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 19 |
A public key is something that is well known, i.e. published.
The server will then use its own private key to decrypt the information.
Let
Properties of F
F(PubKey, M) is encrypted
F(PriKey, M) is encrypted
F(PubKey, M) is different than F(PriKey, M)
M == F(PubKey, F(PriKey, M))
M == F(PriKey, F(PubKey, M))
Given F(key, M) it is hard to find M without the other key
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 20 |
Alice has a secret, M, to communication to Bob in public
Alice computes secret = F(Bob’sPubKey, M)
Alice sends the result to Bob
Bob computes F(Bob’sPriKey, secret ) to get M
It will be hard for anyone else to compute M from secret
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 21 |
Bob has a document, M, that he
Bob computes Doc = F(Bob’sPrivateKey, M)
Bob publishes Doc & his public Key
Since Bob’s public key, F(Bob’sPubKey, Doc), generates the message, Alice knows the message came from Bob
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 22 |
RSA (Rivist, Shamir, Adleman)
DSA (Digital Signature Algorithm)
Java & VisualWorks implement these algorithms
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 23 |
Key contains n & e where
n = p*q, p & q are primes
e relatively prime to (p-1)*(q-1)
p & q must be kept secret
Key contains n & d
d = e -1 mod ((p-1)*(q-1))
Let m be a message such that m < n
Let c be the encrypted message
c = m e mod n
If m >= n then break into block smaller than n and encrypt each block
m = c d mod n
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 24 |
Example is from page 467-8 of Schneier
Let
p = 47.
q = 71.
Then n = p*q = 3337
e = 79.
Then d = 79 -1 mod 3220 = 1019
So Alice’s public key is
n = 3337
e = 79
Alice’s private key is
d = 1019
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 25 |
Let m = 41
To send the message to Alice we compute
c = m e mod n = 41 79 mod 3337 = 875
We send 875 to Alice
Alice computes
cd mode n = 857 1019 mod 3337 = 41
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 26 |
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 27 |
Let M be a message (sequence of bytes)
A one-way hash function f() such that:
MD5 - Message Digest 5
SHA - Secure Hash Algorithm
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 28 |
Alice has a message, M, for Bob
Alice via secure channels sends f(M) to Bob
Alice give M to Trent
Trent delivers M1 to Bob
Bob computes f(M1) and compares it to value from Alice
If f(M1) = f(M) Trent did not modify the message
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 29 |
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
public class SampleCode
{
public static void main(String args[])
throws NoSuchAlgorithmException
{
MessageDigest sha = MessageDigest.getInstance("SHA");
sha.update("Hi mom".getBytes());
byte[] shaHash = sha.digest();
System.out.println(new String(shaHash));
MessageDigest md5 = MessageDigest.getInstance("MD5");
md5.update("Hi mom".getBytes());
byte[] md5Hash = md5.digest();
System.out.println(new String(md5Hash));
}
}
| CS 580 Spring 05 | Doc 4, Some Parsing & Security Slide # 30 |
Load the MD5 & SHA parcels & in workspace do
MD5 hash: 'Hi mom' #[114 83 12 28 50 54 225 209 32 37 154 83 76 243 148 235]
SHA hash: ‘Hi mom’ #[98 21 61 218 186 198 119 88 241 144 60 211 87 250 5 236 219 187 235 16]
Convenience method
(SHA hash: 'Hi mom' ) asHexString '62153DDABAC67758F1903CD357FA05ECDBBBEB10'
Copyright ©, All rights reserved.
2005 SDSU & Roger Whitney, 5500 Campanile Drive, San Diego, CA 92182-7700 USA.
OpenContent license defines the copyright on this document.