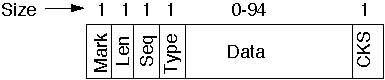| CS 696 Emerging Technologies: Distributed Objects |
|
|---|
Spring Semester, 1998
Networks
To Lecture Notes Index
© 1998, All Rights Reserved, SDSU & Roger Whitney
San Diego State University -- This page last updated 21-Apr-98
Contents of Doc 1, Networks
- References
- Networks
- How Information is Transmitted in a Network
- Store-and-Forward Packet-Switching Networks
- Multiple-Access Networks
- Classes of Communication Services
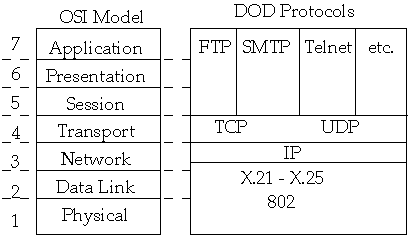
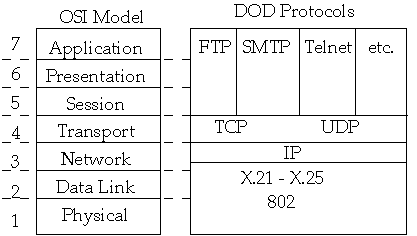
- ISO OSI Model
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
- Layers Pattern
- Context
- Problem
- Forces
- Solution
- Dynamics
- Implementation
- Consequences
- Variants
- Our View of Network Communication with TCP/IP
Communication Networks: A First Course by Jean Walrand, 1991, chapters 2
- 4, 6, 7
Unix Network Programming by W. Richard Stevens, 1990, selected pages
Internetworking with TCP/IP Volume 1 Principles, Protocols, and
Architecture, Third Edition, by Douglas E. Comer, selected pages
RFC 1700, Assigned Numbers by J.Postel
Pattern-Oriented Software Architecture: A System of Patterns, by
Buschmann, Meunier, Rohnert, Sommerlad, Stal, 1996, pages 31-52
Point-to-point
- Dedicated link between two computers
Communication Network
- A set of communication nodes that are interconnected to permit the exchange
of information
StringNet
Information transferred to medium
Network Protocols - handshaking
Duplex
Store and forward
Flow control
Routing
Information is transformed into electrical or optical signals
All signals are corrupted during transmission
Transmission adds noise to the signal
Digital data helps over come noise
-
- Slightly corrupted 1's are distinguishable from slightly corrupted 0's
-
- Digital data allows for error-control
Dynamic data like audio or video normally requires continuous transmission
Packets
Stream of bits is divided into separate packets
Kermit Packet Structure
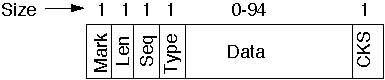
Mark
- Start of packet, usually control A
Len
- length of packet in ASCII characters
Seq
- Packet sequence number mod 64
Type
- D = data
- Y = acknowledge (ACK)
- N = negative acknowledge (NACK)
- S = send initiate
- R = receive initiate
- etc.
Data
- The data if any
CKS
- Checksum
Student Net
Show:
- Packet order
-
- Lost packets
-
- Multiplexing of channels
Routing
- What paths should the packets follow in the network
Flow Control
- How to regulate the flow so parts of the network don't become
congested
Addressing
- How to specify addresses of devices on the network
Security
- Maintain privacy of information on the network
Standards
- Needs standards to allow multiple vendors to build compatible hardware and
software
Presentation
- Enable many different types of terminal equipment to communicate
Switching
Circuit switching
-
- A direct line between to users is established
-
- The users "own" the line until they drop the connection
-
Virtual - circuit switching
-
- All packets of a stream follow the same route
-
- Used by ATM (Asynchronous Transfer Mode )
-
Datagram packet - switching
-
- Each packet is routed individually
-
- All packets of a stream may or may not take the same route
-
- Used by TCP/IP
Multiple computers share a single communication channel
Examples
- Ethernet
- Token Ring
- Appletalk
- Starlan
Multiplexing - How to share a communication channel
- Frequency - Division Multiplexing ( FDM )
-
- Assign different frequencies to different users
-
-
- Time - Division Multiplexing ( TDM )
- Divide the time into small slices
- Each user gets every N'th time slice
- Statistical Multiplexing
-
- Give each user a label
- Mark packets with label
- Mix packets from different users on channel
-
Local Air Net
Show:
- FDM
- TDM
End-to-end services as seen by the users:
Synchronous communications
- Bit stream is delivered with a fixed delay and given error rate
-
- Each bit reaches the destination with the same time delay after leaving the
source
Asynchronous communications
- Bit stream is divided into packets
-
- Packets are received with varying delays, so packets can arrive out of order
-
- Some packets are not received correctly
-
- Connection-oriented
- Packets are delivered in order
-
- System confirms delivery and put packets in order
-
- Error free
-
- Connectionless
- Packets are treated individually
-
- Program has to worry about order, error and lost packets
- Expedited Data
- Faster delivery than normal
ISO - International Organization for Standardization
OSI - Open Systems Interconnection reference model
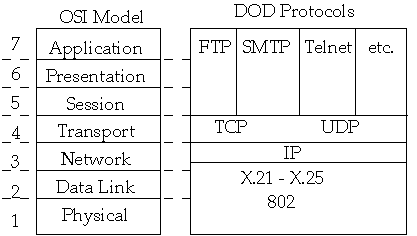
Transform bit to signal and signal to a bit
Medium used to transmit signal
- radio,
- twisted pair
- coaxial cable
- optical fiber
Issues
- Noise
- Attenuation - signal decreases in strength
- Dispersion - signal changes
- Echoes
Examples
- modems
- RS-232
- V.24
Makes sure that a packet arrives properly between two ends of a wire
ACK -acknowledgment of packets
Error detection
Store and forward
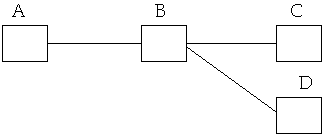
Deals with getting a packet from the source node to destination node in the
network
Issues
- Routing
- Congestion
- Addresses of physical devices
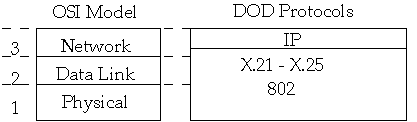
Controls the delivery of messages between the end nodes in the network
Issues
- Divide message into packets
-
- If required reorder packet that arrive out of order
-
- If required resend lost or damaged packets
-
- End to end flow control
-
Negotiates the rules used in the session
Full duplex or half-duplex, etc.
Syntax translation between computers
Byte order
Encryption
Data compression
Whatever the program was designed to do
A large system that requires decomposition
Designing a system that is primarily a mix of low- and high-level issues
Examples of low level issues
- Reading bits from a file
- Reading electrical signals from a wire
- Hardware traps
- Sensor input
- Hardware dependencies
Late source code changes should not ripple through the system
Interfaces should be stable
Parts of the system should be exchangeable
May build other systems with same low-level issues
Similar responsibilities should be grouped to help understandability and
maintainability
No standard component granularity
Complex components need further decomposition
Crossing component boundaries may impede performance
System will be build by a team of programmers and work has to be subdivided
along clear boundaries
Divide system into layers
Layer K provides services to Layer K+1
Layer K may delegate subtasks to Layer K - 1
Layer K interacts with only K+1 and K-1 for K = 2, 3, ..., N-1
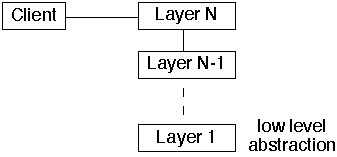
1. Complete Top-Down
- Client issues request to Layer N
-
- This causes subrequests to sent to:
- Layer N-1, then to
- Layer N-2, then to
- Layer N-3, etc. to
- Layer 1
-
- Layer N then returns response to client
2. Top-Down
- Client issues request to Layer N
-
- This causes subrequests to sent to:
- Layer N-1, then to
- Layer N-2, then to
- Layer K > 1, which can satisfy all subrequests
-
- Layer N then returns response to client
3. Complete Bottom-Up
- Layer 1 detects some event
- Layer 1 notifies layer 2
- Layer 2 notifies layer 3
- etc.
- Layer N notifies client
Dynamics Continued
4. Bottom-Up
- Same as complete bottom-up but some layer K is able to deal with the
event
5. Communicating stacks of layers
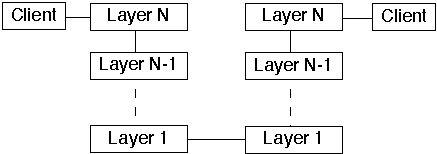
Define the abstraction criterion for grouping tasks into layers
Determine the number of abstraction level
Name the layers and assign tasks to each of them
Specify the services
Refine the layering
Specify an interface for each layer
Structure individual layers
Specify the communication between adjacent layers
Decouple adjacent layers
Design an error-handling strategy
Benefits
Reuse of layers
Support for standardization
Dependencies are kept local
Exchangeability
Liabilities
Cascades of changing behavior
Lower efficiency
Unnecessary work
Difficulty on establishing the correct granularity of layers
Relaxed layered system
- Each layer can use the services of all layers below it
-
- This may gain flexibility and/or performance but losses in maintainability
Layering through Inheritance
- Ties higher level to lower level
TCP - Connection-oriented
UDP - Connectionless
TCP gives us a "pipe" between machines to allow us to send messages between
machines
Addresses and Names
IP address is a 32 bit number
- 130.191.226.1
Machines on a network need a unique IP address
Domain Name System ( DNS )
- rohan.sdsu.edu
| Domain Names | Meaning |
| COM | Commercial organizations |
| EDU | Educational institutions |
| GOV | Government institutions |
| MIL | Military groups |
| NET | Major network support groups |
| ORG | Organizations not list above |
| ARPA | obsolete |
| INT | International organizations |
| country codes | 2-letter code per country |
IP addresses and names are assigned by Internic
Ports
Each TCP/IP machine has multiple logical communication channels called ports
Ports are numbered from 0 - 65536
A connection between two machines is uniquely defined by:
- the protocol (TCP or UDP)
- the IP address of local machine
- the port number used on the local machine
- the IP address of remote machine
- the port number used on the remote machine
| reserved port numbers | 1 - 1023 |
| port numbers used by system | 1024 - 5000 |
Some Interesting Servers
| Service | Port Number |
| echo | 7 |
| discard | 9 |
| character generation | 19 |
| daytime | 13 |
| time | 37 |
| telnet | 23 |
| gopher | 70 |
| WWW | 80 |
See RFC 1700 for a complete list for reserved ports and services they
provide
Telnet a Simple Client
On rohan type:
- telnet saturn 13
Or try:
- telnet www-rohan 80
-
- then type anything followed by <CR>
Or try:
- telnet www-rohan 80
then type:
- GET / HTTP/1.0 <CR>
- <CR>
- <CR>
RFC's
Request for Comments define the internet protocols
See:
http://www.yahoo.com/Computers_and_Internet/Standards/RFCs/
http://www.cis.ohio-state.edu/hypertext/information/rfc.html
 visitors since 27-Jan-98
visitors since 27-Jan-98